Plug & Play Log Consolidation
Group related logs & deduplicate their redundant values
Save 90% of your SIEM Ingest volume and costs
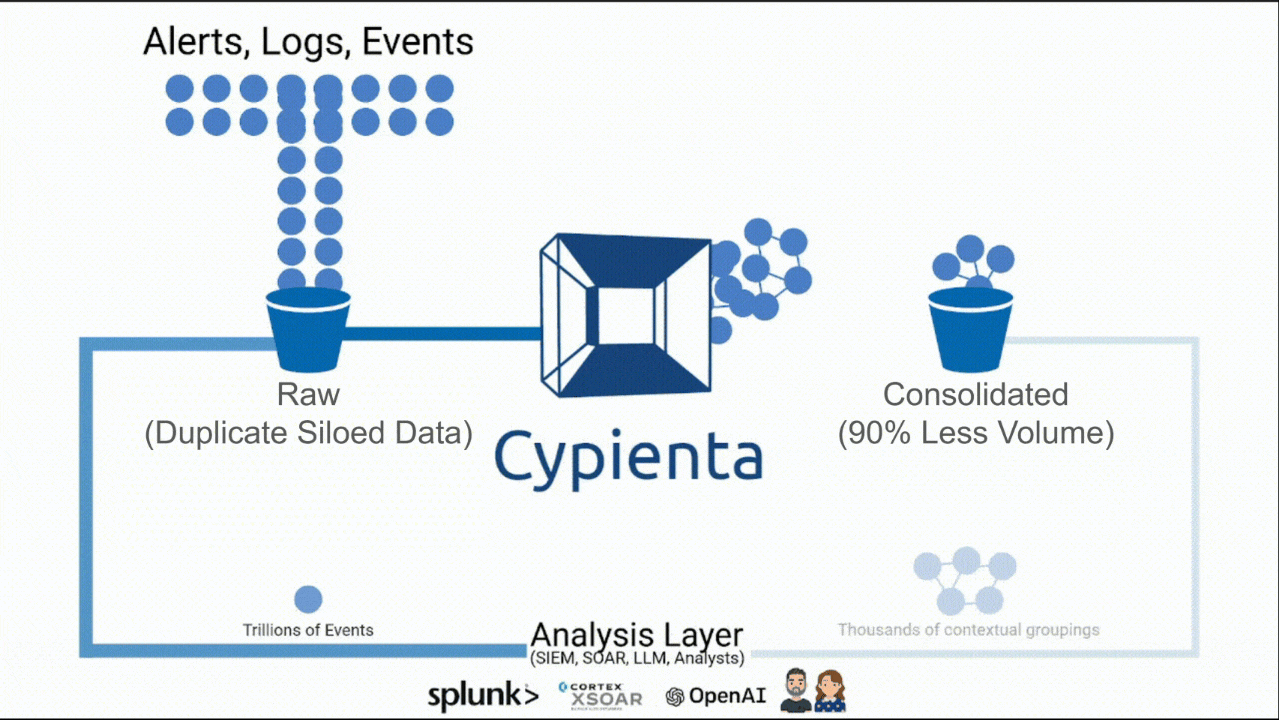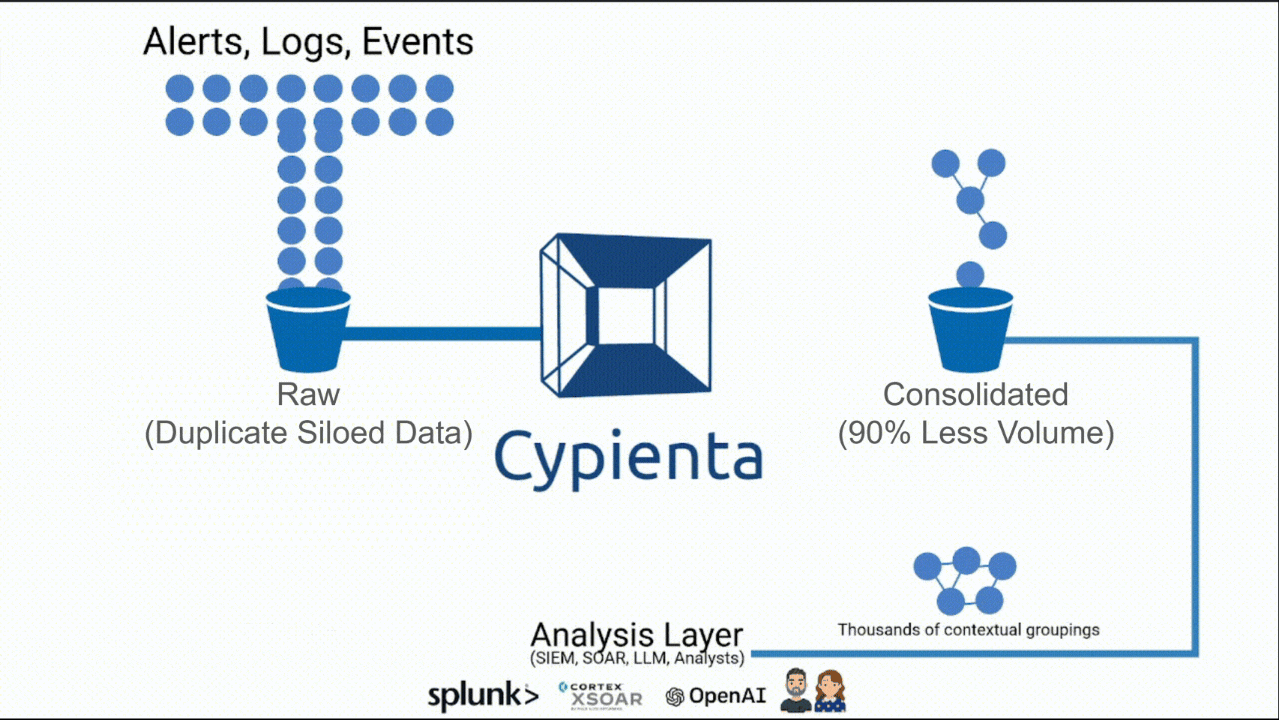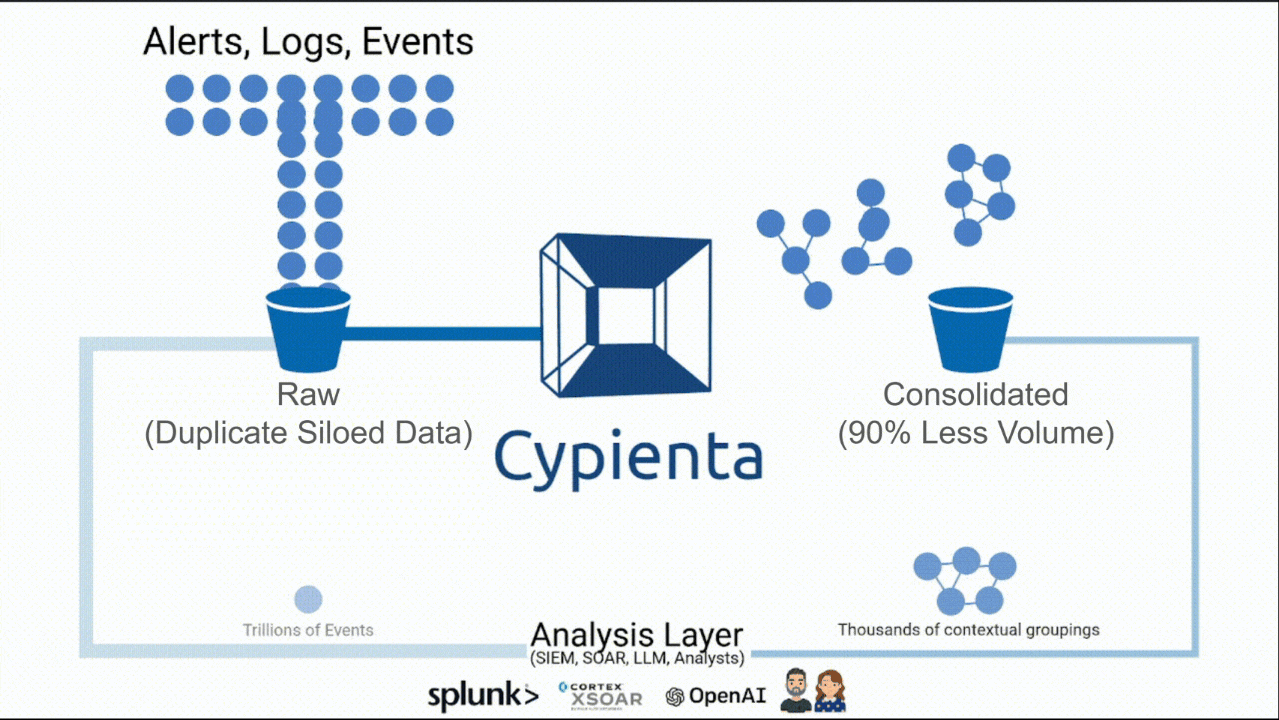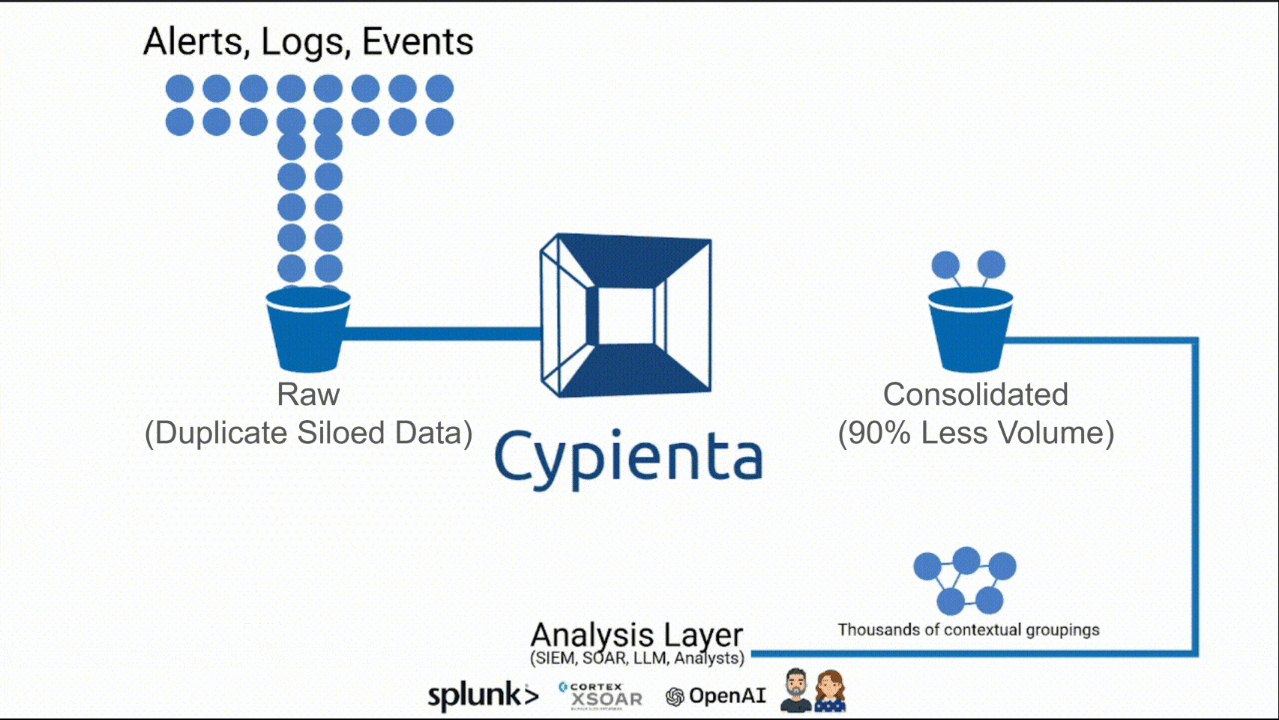
The Missing Layer Between Expanding Detection and Effective Analysis
Contextual, Semantic & Causal Consolidation that scales.
Smaller volume. Bigger insight.
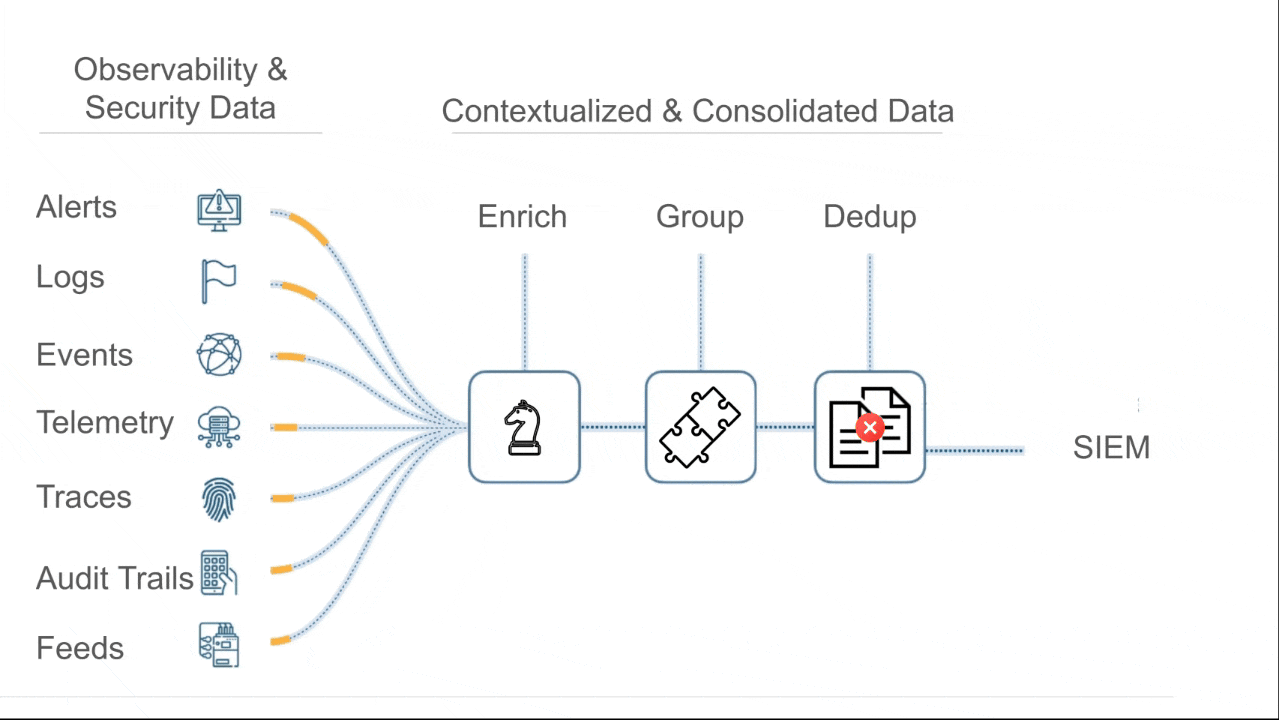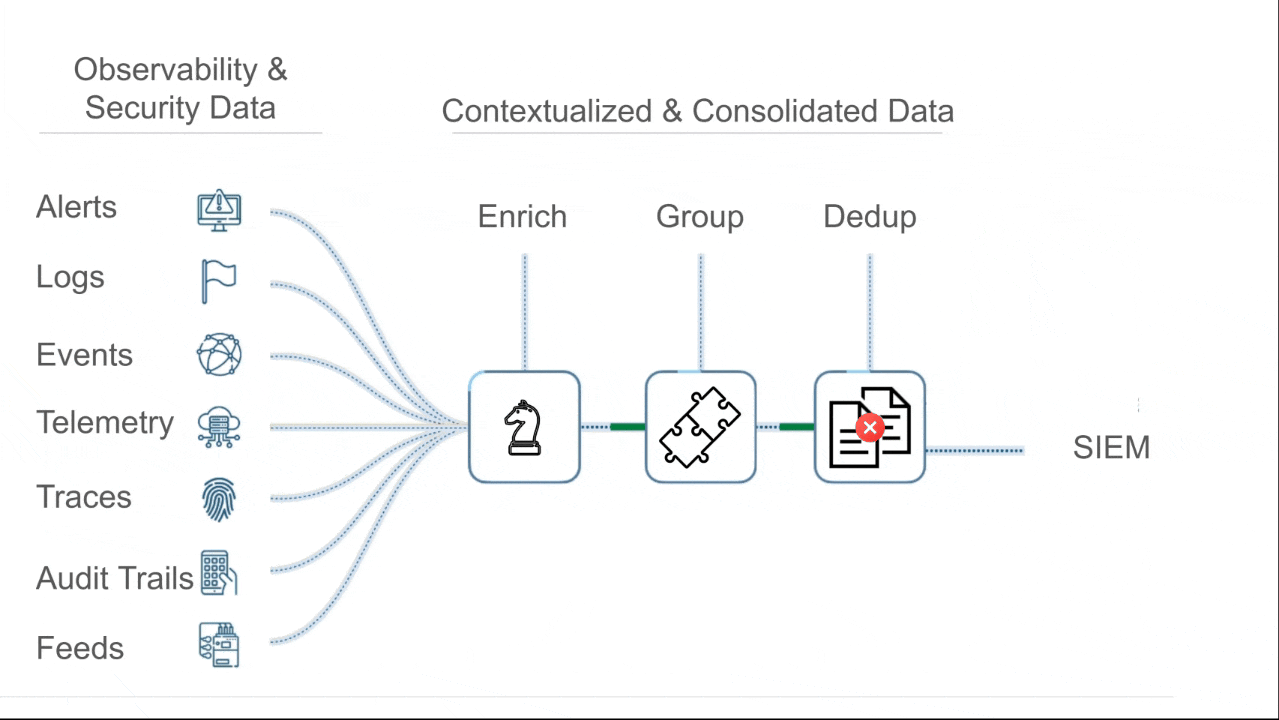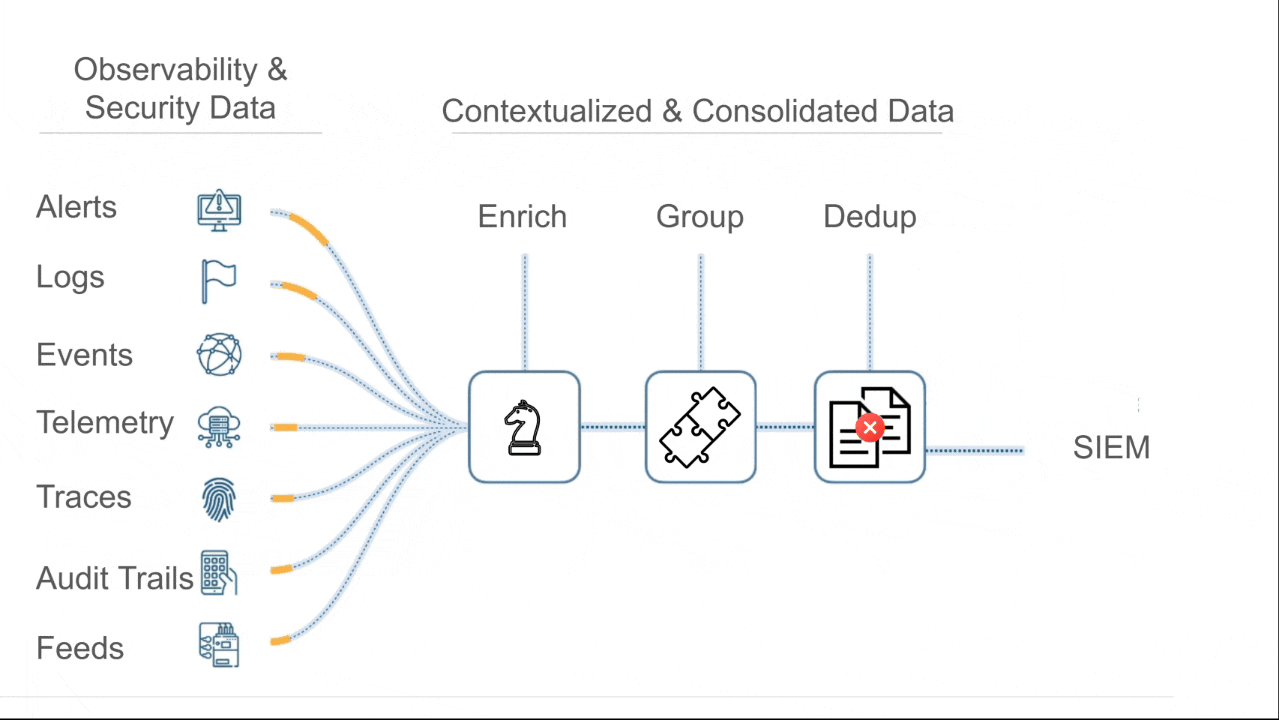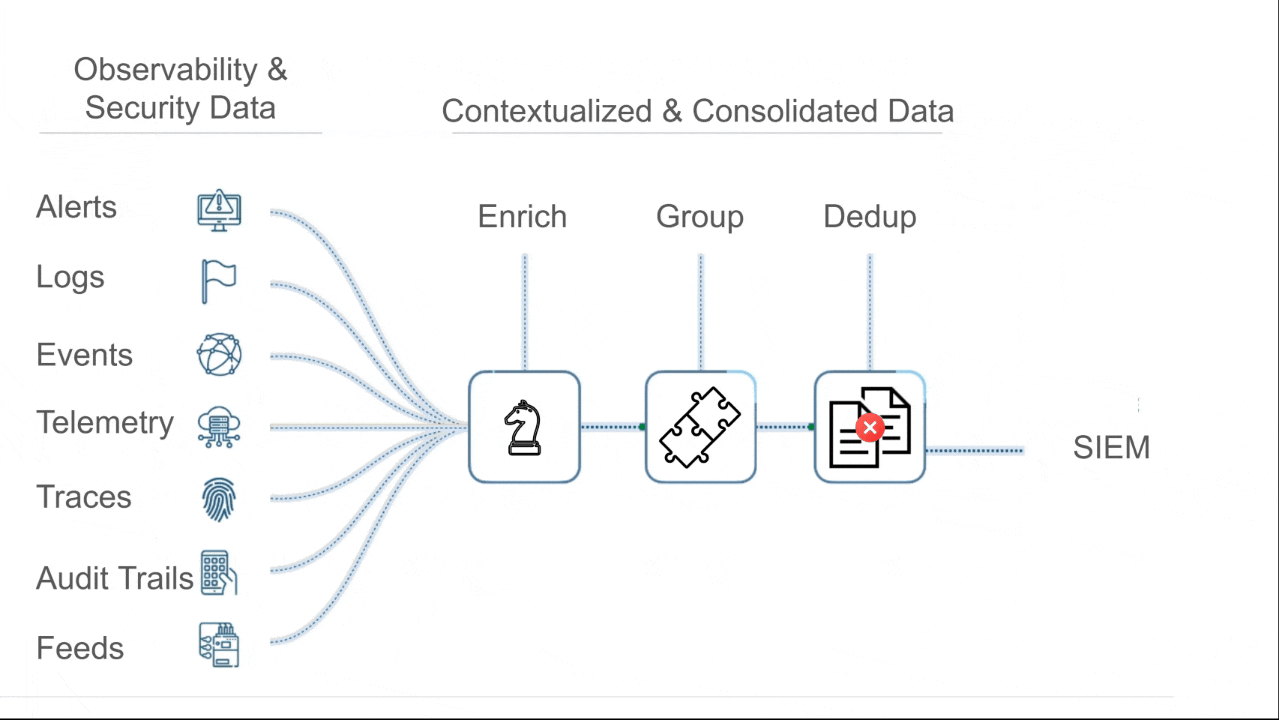
Cypienta groups events, alerts, logs, & telemetry from all sources, then hands consolidated, contextualized groupings to SIEM, SOAR, & AI so they can reason on fewer, richer, interconnected units of data.
A 10X efficiency and efficacy boost for your people, process & tools.
AS FEATURED IN
%20(1).png)

%20(12).png)
%20(11).png)
%20(5).png)
%20(3).png)
%20(8).png)
%20(6).png)
%20(2).png)

%20(15).png)
%20(9).png)
%20(7).png)
The Context Layer Your SOC’s Been Missing
Automatically group related events based on causality and similarity.
Stop chasing isolated alerts and start tracking real attack narratives, from any source.
Smart Data In, Sharp Decisions Out.
It’s not just about reducing what you ingest, it’s about understanding what truly matters. Cypienta groups the noise, contextualizes the signal, and connects the dots others miss.
Consolidating redundant data, but keeping the full picture.
Lower SIEM Costs
Slash ingestion and compute by processing smarter data, with deduplicated groupings.
Context Groups
Events are grouped by similarity & causality across event type, involved assets, time proximity, behavioral patterns, and known threat structures.
Fewer LLM Calls
Provide AI copilots with rich, contextual input,
not raw & noisy data,
so you reduce token use and improve accuracy.
You are spending too much, processing noise.

Connect the dots
Root cause and attack flow insight not false positives and lone incidents.
SOCs today spend 10x💰 what they should on tech!
These inflated tech stack costs are eating at workforce budgets.
Tool/Area | Without Cypienta | With Cypienta | Savings Impact |
|---|---|---|---|
SIEM | Ingests siloed, isolated, and disparate raw, duplicated logs; expensive storage and compute for enrichment & correlation searches. | Only contextualized, enriched & correlated incidents ingested; More comprehensive insights available faster via searches; minimal licensing, compute, and storage. | 60%+ savings on SIEM compute and storage |
SOAR | Multiple triggered workflows for alerts of the same root cause, repeated workflows for similar, related and causal events; fails or stalls often on incomplete incidents. | Workflows start with full incident context and root cause and are more effective at remediation. | 40%+ savings on SOAR with fewer & smarter workflows |
AI Analysts, Agents & Copilots | Multiple prompts and inferences for alerts of the same root cause, repeated inferences for similar, related and causal events. | Works on fully correlated and enriched incident groups; minimal licensing, compute, and storage. | 80%+ savings on LLMs and AI agents inferences with optimized context-rich prompts & calls |
Ticketing & Case Management | Multiple alerts & tickets for alerts of the same root cause, repeated tickets for similar, related and causal events. | Single, comprehensive & contextualized case per incident; minimal licensing, compute, and storage. | 30%+ savings on ticketing & case management with compact, contextualized & rich tickets |
SOC Staffing | Overloaded staff doing repetitive triage and redundant investigations for alerts of the same root cause, repeated investigations and hunts for similar, related and causal events. | Incidents are triaged and contextualized comprehensively and efficiently with root causes, historical learnings, similar incidents and causal sequences identified. | Reduce more than 35 hours a week of tedious work in your SOC |
















.png)